Fight back against Zoom-bombing using MobileIron UEM and Threat Defense!
*This post originally appeared on the MobileIron blog prior to the acquisition in December 2020, when MobileIron became part of Ivanti.
As people around the globe work from home due to the COVID-19 pandemic, Zoom’s video conferencing tool has risen in popularity among both users and hackers. Several high-profile security vulnerabilities have recently been discovered, with research studies and opinion articles hitting the news almost daily. Zoom has been quick to take action, posting frequent updates on their blog and announcing a 90-day freeze on new features to address all of these security vulnerabilities.
The most notable vulnerability, known as “Zoom-bombing,” involves pranksters crashing public meetings and private teacher lectures. While pranksters can randomly guess Zoom meeting IDs (a meeting ID is made up of 9, 10 or 11-digit numbers) and passwords, actual lecture and meeting attendees have been posting these details to social media like Twitter and Reddit, and onto Zoom Raid Discord servers where people sign up to receive this information. Uninvited Internet trolls then disrupt Zoom meetings by exploiting the Share Screen feature and displaying pornographic or disturbing images to the unsuspecting attendees.
Recently, Zoom enabled a meeting password and waiting room by default to help mitigate these attacks for new sessions. This is a start, but there are other countermeasures that meeting hosts and corporate IT administrators can take to further mitigate Zoom-bombing raids. Here are the steps that the meeting host can take: Require a meeting password (this is now enabled by default); enable a waiting room (this is now enabled by default); limit who can share information (for example, only allow the host to share information); lock the meeting when everyone has joined; avoid posting public links to your meetings; and avoid posting actual Zoom meetings onto social media (the Meeting ID is displayed - there are privacy issues!).
The following sections itemize the tasks corporate IT administrators can follow to secure Zoom meetings on iOS, iPadOS, and Android Enterprise mobile devices, and macOS and Windows 10 laptops, that are managed by MobileIron’s unified endpoint management (UEM) platform. MobileIron Threat Defense (MTD) can also be enabled on iOS, iPadOS, and Android Enterprise mobile devices to protect against mobile device threats, as threat actors are creating malware and malicious exploit kits that can attack these Zoom vulnerabilities. Threat actors are registering COVID-19 and coronavirus Internet domain names and then spinning up websites to phish unsuspecting visitors to their sites in order to deliver the malware and exploit kits onto mobile devices, laptops, and desktops. Keep the antivirus agent up to date on your laptops and desktops. MobileIron UEM can configure Microsoft Advanced Threat Protection on macOS and Windows 10 laptops and desktops.
iOS/iPadOS configuration
The first step is to add the latest Zoom Cloud Meetings app from the iOS App Store to the MobileIron Cloud (or MobileIron Core) App Catalog.
Configure a managed app configuration to enforce the controls depicted below. Then silently install the managed Zoom Cloud Meetings app onto the device when the user successfully enrolls their mobile device to MobileIron UEM.
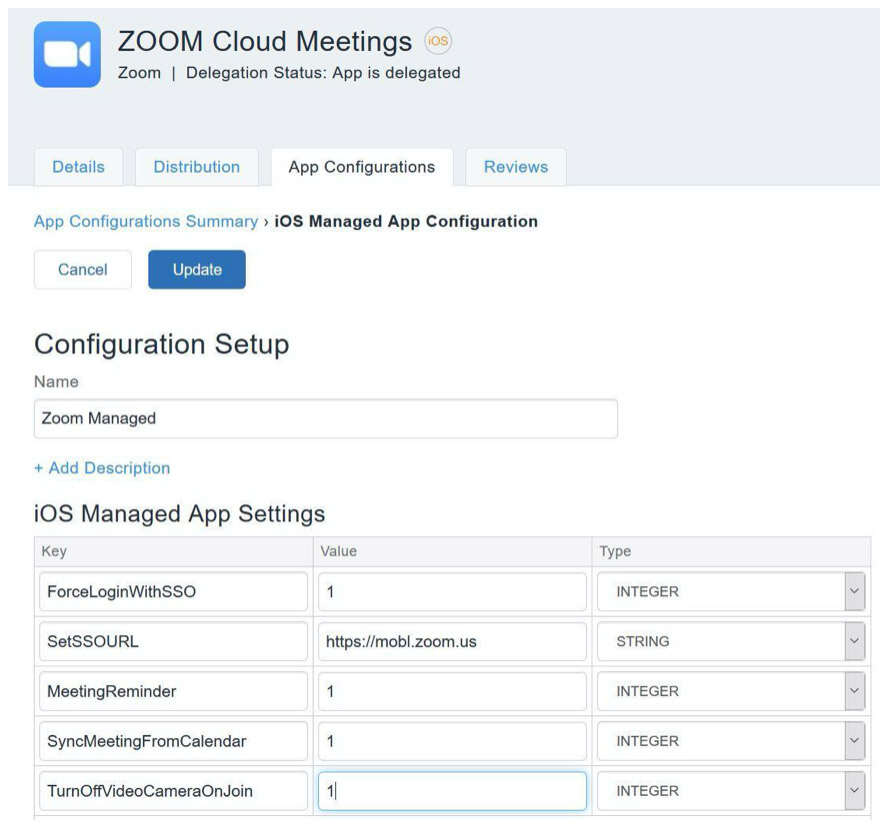
If the iOS or iPadOS device falls out of compliance or a mobile threat is detected by MobileIron UEM or MTD, the managed Zoom Cloud Meetings app and its content can be removed to protect the user’s personal and work data from loss or theft.
Android Enterprise configuration
Again, the first step is to add the latest Zoom Cloud Meetings app from the Google Play Store to the MobileIron Cloud (or MobileIron Core) App Catalog.
For Android devices like Samsung and Pixel phones and tablets, enable Android Enterprise. Then approve the Zoom Cloud Meeting app to be a managed app and be configured for a managed configuration to apply the security controls itemized below and then silently install onto these Android devices.
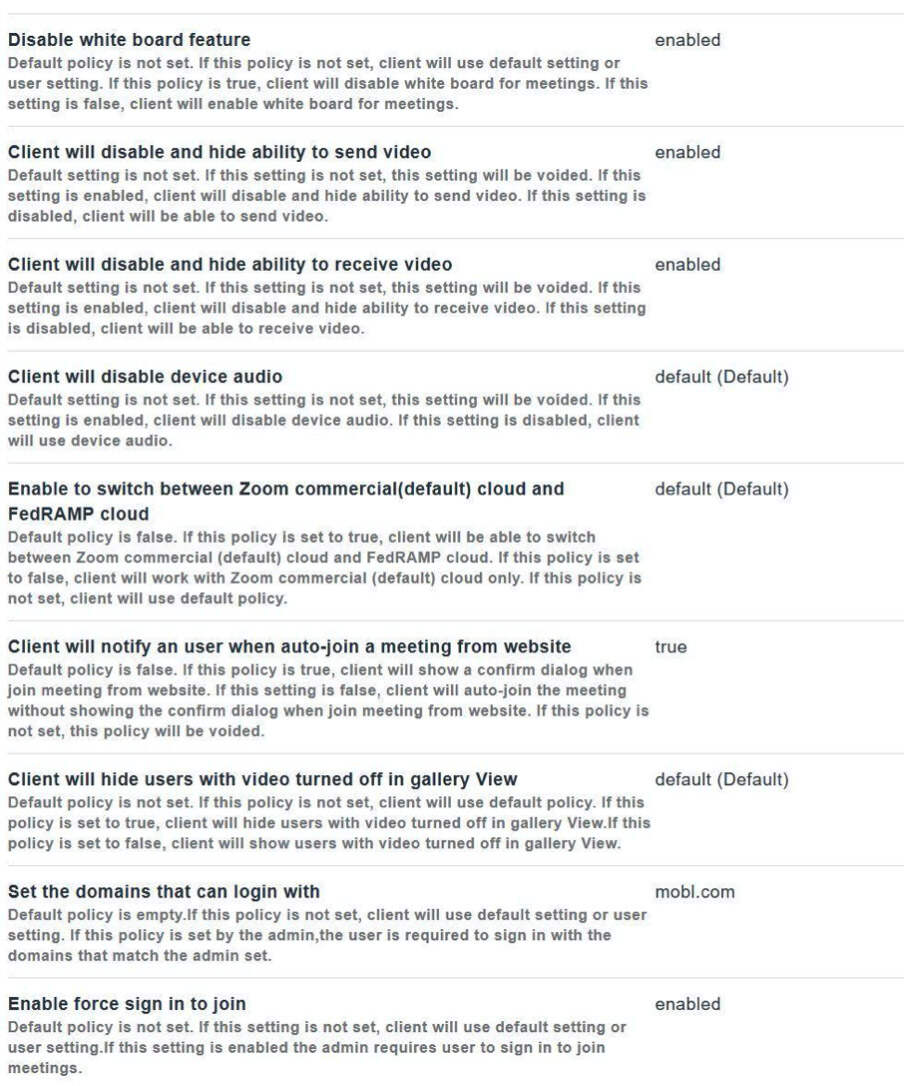
Here is a Zoom article that explains these security controls further. And below is a screenshot of an example for the Android managed configuration for the Zoom Cloud Meetings app on MobileIron Cloud UEM using the following control settings and more.
General settings
Disable Google login option
Disable Facebook login option
Disable Email login option (Set this to 0 or false to enable)
Set the email address domain that users can login with
Meeting settings
Disable Screen Share when starting or joining a meeting
Disable in-meeting chat
Disable in-meeting file transfer (sending or receiving files)
Disable local recording
Disable cloud recording
Disable sending video
Disable receiving video
Enable mirroring of shared video (Set this to 0 or false to disable)

Like iOS and iPadOS devices, if an Android Enterprise device falls out of compliance or a mobile threat is detected by MobileIron UEM or MTD, the managed Zoom Cloud Meetings app and its content can be removed or hidden to protect the user’s personal and work data from being compromised.
macOS configuration
For macOS laptops and desktops, you can download the package installer file directly from Zoom here: https://zoom.us/client/latest/ZoomInstallerIT.pkg. Then add and upload the package file into the MobileIron Cloud or MobileIron Core App Catalog as an In-House app.
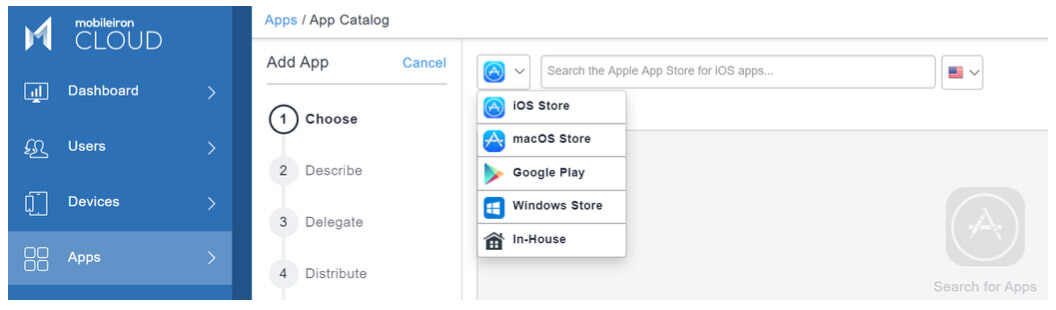
Then use a PLIST to provision the security controls required to secure the Zoom Desktop Client app. An example of the PLIST that can be used by appending the security controls shown below is here:
https://support.zoom.us/hc/en-us/article_attachments/360042873691/us.zoom.config.plist.
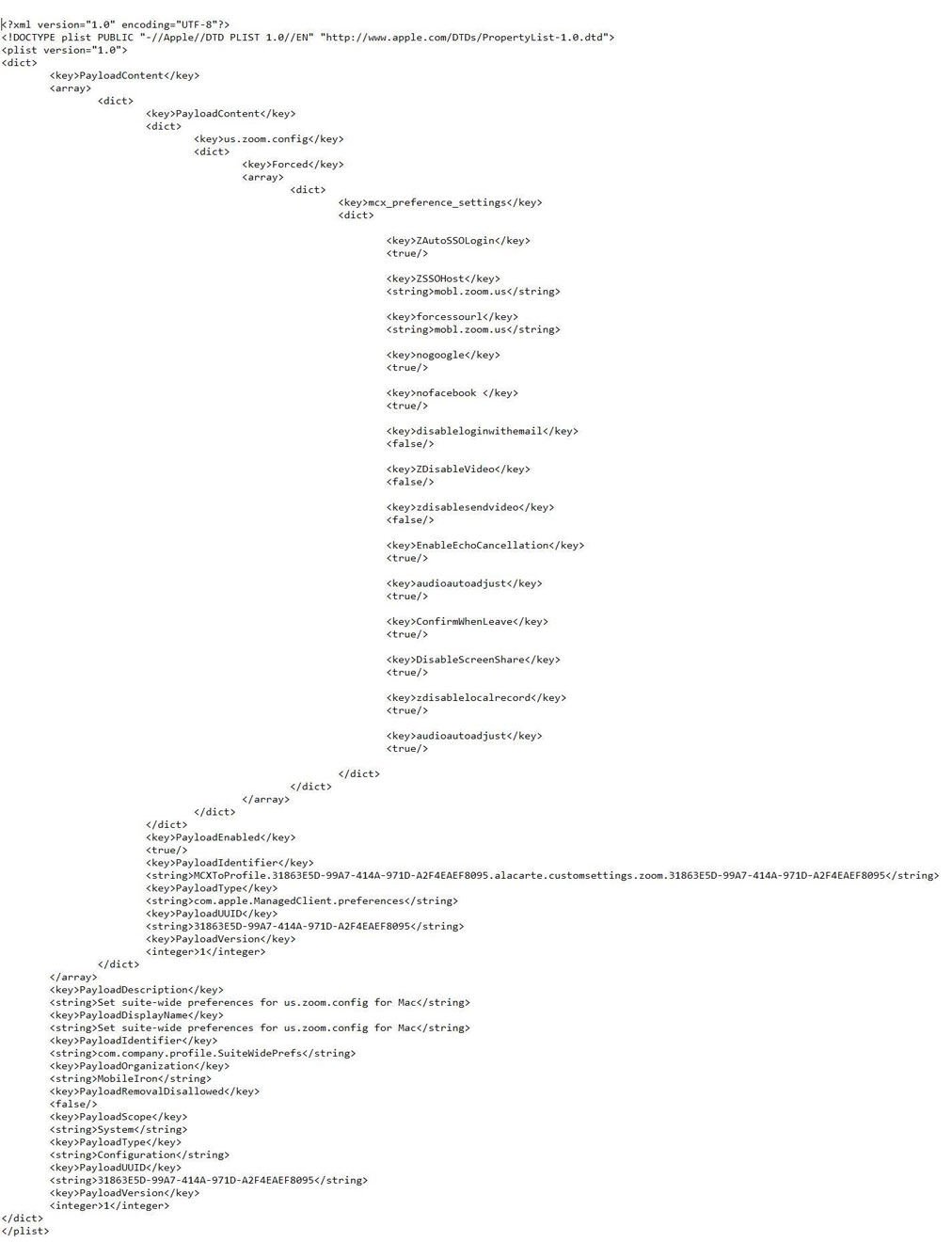
General settings
Disable Google login option
Disable Facebook login option
Disable Email login option (Set this to 0 or false to enable)
Set the email address domain that users can login with
Meeting settings
Disable Screen Share when starting or joining a meeting
Disable in-meeting chat
Disable in-meeting file transfer (sending or receiving files)
Disable local recording
Disable cloud recording
Disable sending video
Disable receiving video
Enable mirroring of shared video (Set this to 0 or false to disable)
A further explanation of the control settings can be found here.
Afterward, go to the MobileIron Cloud or MobileIron Core configuration and select Custom Configuration. Upload the PLIST file into the configuration. Save the configuration and then distribute to the macOS laptop and desktop users or group.
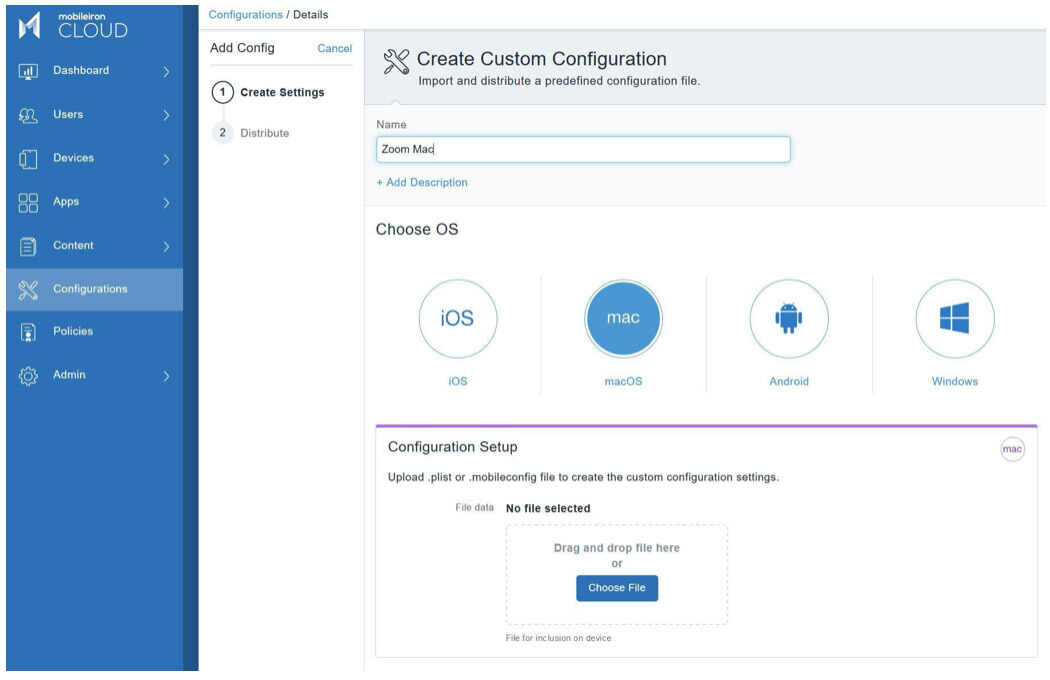
Windows 10 configuration
For Windows 10 laptops and desktops, the Zoom Desktop Client MSI installed can be downloaded from https://www.zoom.us/client/latest/ZoomInstallerFull.msi. Add and then upload the MSI installer file as an In-House app within the MobileIron Cloud or MobileIron Core App Catalog.
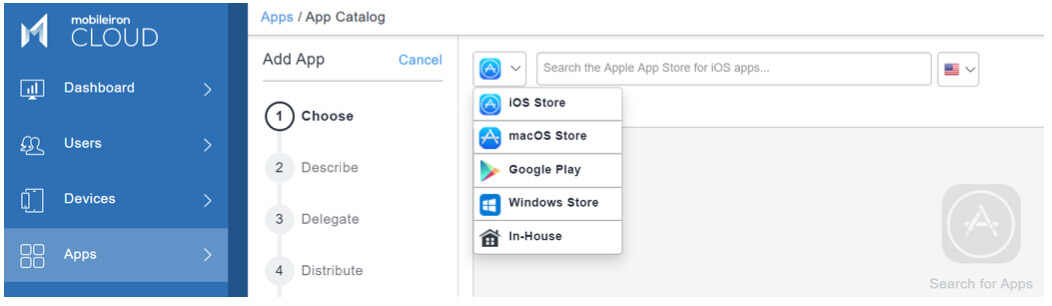
Afterward, upload the Zoom ADMX-template that populates the Windows 10 GPO Settings configuration where the Zoom Desktop Client security controls can be applied. The zipped file is below and can be directly added into MobileIron UEM.
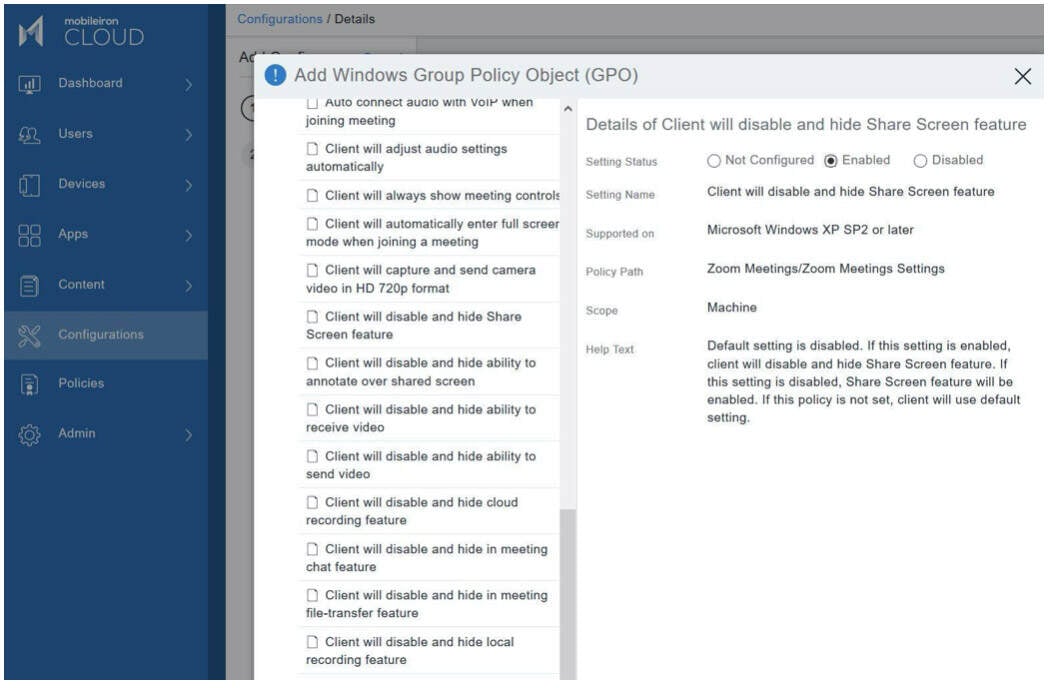
Once the ADMX-template is appended, go to Configurations and then add a Windows GPO Settings configuration. Select Add and expand the Machine settings, and then select Zoom Meetings.
Then drill down to find these settings and configure as recommended below. Save the configuration and then distribute to the Windows 10 laptop and desktop users or group.
General settings
Disable Google login option
Disable Facebook login option
Disable Email login option (Set this to 0 or false to enable)
Set the email address domain that users can login with
Meeting settings
Disable Screen Share when starting or joining a meeting
Disable in-meeting chat
Disable in-meeting file transfer (sending or receiving files)
Disable local recording
Disable cloud recording
Disable sending video
Disable receiving video
Enable mirroring of shared video (Set this to 0 or false to disable)